
A workload identity is a special identity used for authentication and access by software applications and services. It helps them connect to other services and resources securely.
The most direct method for external workloads to use Google Cloud APIs is by using downloaded service account keys. However, this approach comes with two significant challenges:
- Management Complexity: The keys must be stored securely and regularly changed, which can be administratively demanding.
- Security Vulnerability: Since keys are long-term credentials, they are susceptible to compromise, posing a security risk.
To address these issues, workload identity federation offers an alternative. This approach allows applications outside of Google Cloud to replace persistent service account keys with short-lived access tokens. This is accomplished by establishing a trust relationship between Google Cloud and an external identity provider. The external identity provider issues time-limited credentials that applications can use to act as service accounts.
The benefits of this approach include heightened security and reduced management overhead. By using temporary access tokens, the exposure window for potential security breaches is minimized. Additionally, the need for ongoing key management and rotation is diminished.
Google Cloud Workload Identity Federation Primer
https://cloud.google.com/iam/docs/workload-identity-federation
Configuration
To implement workload identity federation, you need to configure the external identity provider to issue trusted tokens. Then, set up Google Cloud’s Identity and Access Management (IAM) policies to permit the external provider to generate tokens on behalf of designated service accounts. Applications can then utilize these short-lived tokens to securely access resources in Google Cloud.
This blog shows how to use workload identity federation to let AWS workloads authenticate to Google Cloud without a service account key.
- In the Google Cloud console, enable the IAM, Resource Manager, Service Account Credentials, and Security Token Service APIs:

- Create the workload identity pool:

- create a provider:
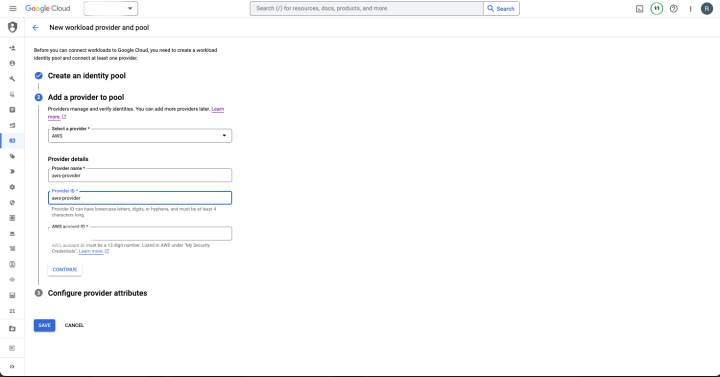
- configure provider attributes:

- Create a service account for the external workload. Grant the service account access to resources that you want external identities to access:

- To allow external identities to impersonate a service account, you grant them the Workload Identity User role
roles/iam.workloadIdentityUser:

Testing
For testing, we will deploy a VM running Linux and install gcloud-cli on it.
- Create a credential configuration:

- Authenticate using the credential configuration exported above:

- run “a few gcloud commands”:

and it works!
References
https://cloud.google.com/iam/docs/workload-identity-federation
https://cloud.google.com/iam/docs/workload-identity-federation-with-other-clouds
